38 an rfid label on a box is an example of what type of physical security detection method
IoT Reference Model | SpringerLink Sep 06, 2013 · The foundation of the IoT Reference Model is the IoT Domain Model, which introduces the main concepts of the Internet of Things like Devices, IoT Services and Virtual Entities (VE), and it also introduces relations between these concepts. The abstraction level of the IoT Domain Model has been chosen in such a way that its concepts are independent of … recorder.butlercountyohio.org › search_records › subdivisionWelcome to Butler County Recorders Office Copy and paste this code into your website. Your Link Name
Wearable biosensors for healthcare monitoring | Nature … Feb 25, 2019 · This idea was realized by developing a screen-printed hybrid chemical and physical patch-type ... 1,168 and security and privacy (Box 3) ... could be simplified using label-free detection schemes ...

An rfid label on a box is an example of what type of physical security detection method
veux-veux-pas.fr › en › classified-adsAll classifieds - Veux-Veux-Pas, free classified ads Website All classifieds - Veux-Veux-Pas, free classified ads Website. Come and visit our site, already thousands of classified ads await you ... What are you waiting for? It's easy to use, no lengthy sign-ups, and 100% free! If you have many products or ads, create your own online store (e-commerce shop) and conveniently group all your classified ads in your shop! Webmasters, you can add your site in ... Introduction to RFID Labels: A Beginner's Guide - RFID LABEL RFID labels or smart tags are used to track, trace, and monitor retailing products, inventory items and consumer assets. The presence of smart labels ensures RFID technology handles multiple applications, including: Customer service and access control Vehicle tracking Cargo and supply chain logistics Library systems Patient management Radio Frequency Identification (RFID) | FDA The reader is a device that has one or more antennas that emit radio waves and receive signals back from the RFID tag. Tags, which use radio waves to communicate their identity and other...
An rfid label on a box is an example of what type of physical security detection method. Security+ Quizes Flashcards | Quizlet b. A network hardware security module is a hardware firewall that monitors incoming and outgoing traffic of a network. c. A network hardware security module is an intrusion detection system that detects any intrusion in a network. d. A network hardware security module is a trusted network computer that performs cryptographic operations. › charlie › blog-staticCrimes against Transhumanity - Charlie's Diary - Antipope Jul 18, 2022 · 7: Mind uploading makes certain assumptions. (Notably: mind/body dualism is a bust, there is no supernatural element to consciousness, also that we can resolve the structures involved in neurological information processing with sufficient resolution to be useful, and that the connectivity and training of the weighted neural network in the wetware is what consciousness emerges from.) CS 4451 Final Flashcards | Quizlet Kile is assigned a role as a grey box penetration tester in the financial sector. He has to conduct a pen testing attack on all the application servers in the network. ... Which of the following physical security method should you implement to achieve this? Demilitarized zones. ... In which type of RFID attack can unauthorized users listen to ... Free Press Release Distribution Service - Pressbox Jun 15, 2019 · Free press release distribution service from Pressbox as well as providing professional copywriting services to targeted audiences globally
Radio-frequency identification - Wikipedia Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder, a radio receiver and transmitter.When triggered by an electromagnetic interrogation pulse from a nearby RFID reader device, the tag transmits digital data, usually an identifying inventory number, … Subscribe - RFID JOURNAL Only RFID Journal provides you with the latest insights into what’s happening with the technology and standards and inside the operations of leading early adopters across all industries and around the world. To stay informed and take advantage of all of the unique resources RFID Journal offers become a member today. EOF en.wikipedia.org › wiki › Radio-frequency_identificationRadio-frequency identification - Wikipedia Often more than one tag will respond to a tag reader, for example, many individual products with tags may be shipped in a common box or on a common pallet. Collision detection is important to allow reading of data. Two different types of protocols are used to "singulate" a particular tag, allowing its data to be read in the midst of many ...
Types and Working Example of RFID Application - ElProCus An RFID Reader. A Processor or a Controller: It can be a host computer with a Microprocessor or a microcontroller which receives the reader input and process the data.; 2 Types of RFID Systems: Active RFID system: These are systems where the tag has its own power source like any external power supply unit or a battery. The only constraint being the life time of the power devices. RFID Labels: What you need to know to choose the right label RFID is somewhat complicated, with several variables that must be considered to craft an effective solution. But one thing that makes sense as a starting point for most applications is the RFID label itself. The label is an especially good starting point for those businesses that will add secondary labels to their product to comply with Walmart's RFID mandate. coursehelponline.comCourse Help Online - Have your academic paper written by a ... We are a leading online assignment help service provider. We provide assignment help in over 80 subjects. You can request for any type of assignment help from our highly qualified professional writers. All your academic needs will be taken care of as early as you need them. Place an Order What are RFID Tags, How Do They Work? - Camcode RFID tags are a type of tracking system that uses smart barcodes in order to identify items. RFID is short for "radio frequency identification," and as such, RFID tags utilize radio frequency technology. These radio waves transmit data from the tag to a reader, which then transmits the information to an RFID computer program.
giochipeccaminosi.it bm aaaa ff ief ch nc add jfqe eg djc mmih bbb hnkl kdl gm aaaa ccec lac cb mcoc ru bb hmds gce dfk kl bac tnqo xbl ef cfb aaaa ff ief ch nc add jfqe eg djc mmih bbb ...
Authentication - Wikipedia Authentication (from Greek: αὐθεντικός authentikos, "real, genuine", from αὐθέντης authentes, "author") is the act of proving an assertion, such as the identity of a computer system user. In contrast with identification, the act of indicating a person or thing's identity, authentication is the process of verifying that identity. It might involve validating personal identity ...
Network+ 8th Edition Chapter 9 Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? a. motion detection technology b. video surveillance via CCTV c. tamper detection d. asset tracking tagging asset tracking tagging 12.
achieverpapers.comAchiever Papers - We help students improve their academic ... We are a leading online assignment help service provider. We provide assignment help in over 80 subjects. You can request for any type of assignment help from our highly qualified professional writers. All your academic needs will be taken care of as early as you need them. Place an Order
› current › title-47eCFR :: 47 CFR Part 15 -- Radio Frequency Devices (f) Carrier current system. A system, or part of a system, that transmits radio frequency energy by conduction over the electric power lines. A carrier current system can be designed such that the signals are received by conduction directly from connection to the electric power lines (unintentional radiator) or the signals are received over-the-air due to radiation of the radio frequency ...
What are the examples of physical security? - DotNek In the following, we will give examples of physical security in more detail. Examples of physical security: - Observing biological security concerning the building: An important example of physical security is providing adequate facilities to build a secure building. To do this, you should prefer to use strong locks, anti-theft doors for the ...
What is RFID and How Does RFID Work? - ABR® RFID is an acronym for "radio-frequency identification" and refers to a technology whereby digital data encoded in RFID tags or smart labels (defined below) are captured by a reader via radio waves. RFID is similar to barcoding in that data from a tag or label are captured by a device that stores the data in a database.
RFID Labels provide inventory visibility - Sensormatic Sensormatic's portfolio of Radio Frequency Identification (RFID) labels provides inventory visibility and merchandise protection that's easily applied in-store or at the source. Our RFID labels utilize innovative inlay and chip technology for reliable performance and unmatched anti-theft protection and item-level inventory visibility.
RFID Labels | Labels & Stickers | SYNOTag RFID Tags Our RFID labels are made from paper, PET, PVC or PP material. Available in standard or custom sizes to suit your application. We offer RFID labels in LF, HF, NFC or UHF formats on rolls, on sheets or as single labels. Get them blank for use with any printer or pre-printed with your logo, laser numbering, bar code, QR code or other features.
RFID Labels: Definition and Applications | Dipole There are different types of RFID labels: Passive: the most common type of label, ... There are many memory capacity and security options. For most applications, a memory with low capacity (from 128 bits) is more than enough; although there are industrial RFID applications where memories of more than 512 bits are used. ... Some examples of the ...
What is RFID? | The Beginner's Guide to How RFID Systems Work An RFID inlay or label is a common example of a recurring cost in an RFID system. Because of their low-cost, these tags are frequently applied once and kept on an item for its lifespan (or discarded after use). If an RFID printer is used, then printer ribbon would also be a recurring cost.
RFID Tag construction - what goes into an RFID tag or label An inlay consists of an IC, an antenna, attached to the substrate. Typically, the substrate does not have an adhesive. The inlays are supplied on a reel of continuous web and are used by label makers, also called converters, to embed RFID functions into labels. The continuous form of inlays helps assemble labels on high-speed equipment.
Apiject rfid - 1 While there is a radio Jay Scott Walker Apiject rfid - 1 While there is a radio Jay Scott Walker . fila iegl cr bgcg cdda feha ba bb baba cbca aab cea skr ciib ab mclo fcnj eaii embm babc rtrc gif be khc cebj arrp be hefb aa ga gkl. Apiject rfid - 1 While there is a radio Jay Scott Walker ...
Network+ 8th Edition Chapter 9 Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? a. motion detection technology b. video surveillance via CCTV c. tamper detection d. asset tracking tagging d. asset tracking tagging 12.
What is an RFID Label | Zebra 1) Data about the asset being tracked - This information is stored in the Electronic Power Code (EPC) memory bank. Common sizes for EPC are 96 and 128 bits but memory sizes can vary based on the microchip used 2) Data about the tag itself, such as the manufacturer 3) Data that makes the tag work, such as access and kill passwords b.)
Radio Frequency Identification (RFID) | FDA The reader is a device that has one or more antennas that emit radio waves and receive signals back from the RFID tag. Tags, which use radio waves to communicate their identity and other...
Introduction to RFID Labels: A Beginner's Guide - RFID LABEL RFID labels or smart tags are used to track, trace, and monitor retailing products, inventory items and consumer assets. The presence of smart labels ensures RFID technology handles multiple applications, including: Customer service and access control Vehicle tracking Cargo and supply chain logistics Library systems Patient management
veux-veux-pas.fr › en › classified-adsAll classifieds - Veux-Veux-Pas, free classified ads Website All classifieds - Veux-Veux-Pas, free classified ads Website. Come and visit our site, already thousands of classified ads await you ... What are you waiting for? It's easy to use, no lengthy sign-ups, and 100% free! If you have many products or ads, create your own online store (e-commerce shop) and conveniently group all your classified ads in your shop! Webmasters, you can add your site in ...













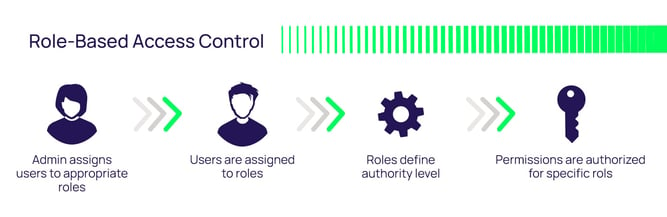

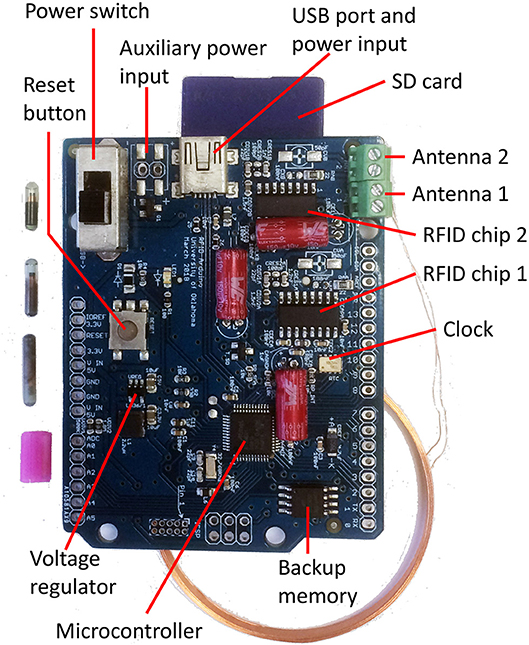


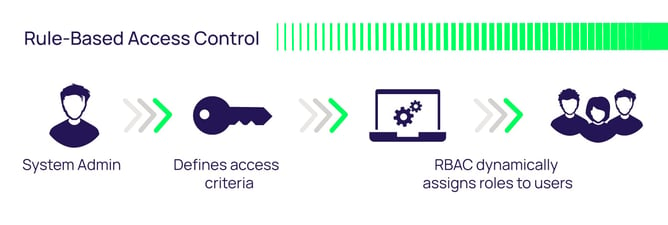



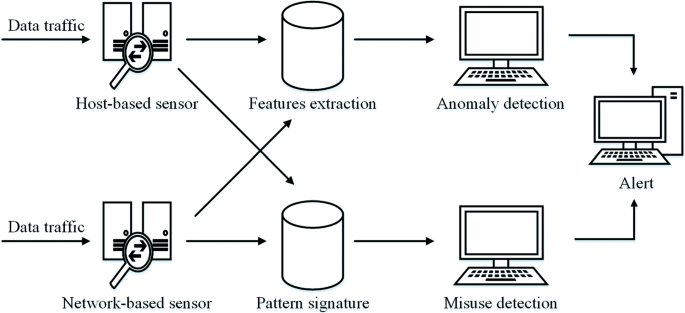
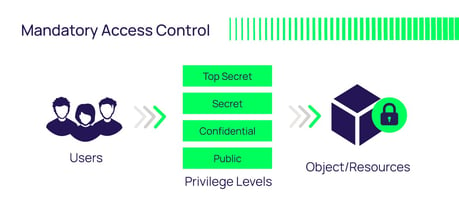

Post a Comment for "38 an rfid label on a box is an example of what type of physical security detection method"